TryHackMe - Block
In this challenge, we have been given on zip file named evidence.zip. We have to extract it and look into the files to answer the questions. This challenge was more of a blue team kind of challenge imo. Let’s start the challenge.
After unzipping the zip file we get two files: lsass.DMP and traffic.pcapng.
What is the username of the first person who accessed our server?
We will use tool called pypykatz to analyze lsass.DMP file. Rune the following command to get minidump from our dmp file:
1
$ pypykatz lsa minidump lsass.DMP
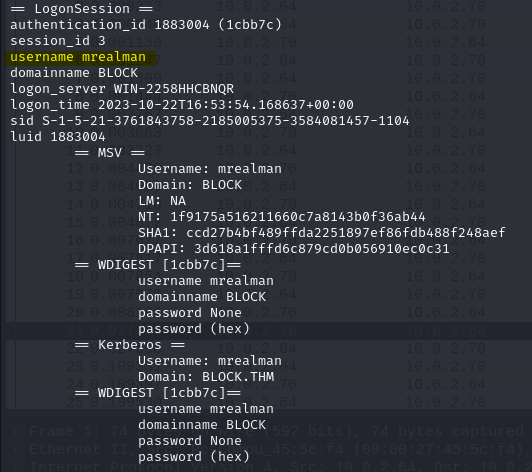
Analyse the output to get username as mrealman
What is the password of the user in question 1?
In the same output, we can get user’s NTHash: 1f9175a516211660c7a8143b0f36ab44 We can use crackstation to crack the hash and get password: Blockbuster1
We will skip question 3 for now.
What is the username of the second person who accessed our server?
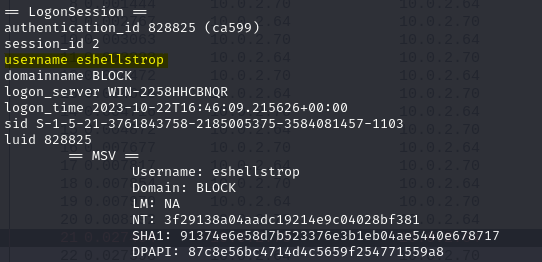
After scrolling a bit in the same output, we can get our second user as answer: eshellstrop
What is the hash of the user in question 4?
We can get NT hash for the user the from the same output. I tried to crack this hash from crackstation but was not able to do it, but we only require hash as our answer: 3f29138a04aadc19214e9c04028bf381
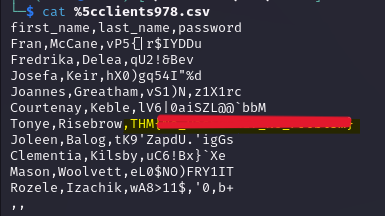
What is the flag that the first user got access to?
Back to question 3, it was tricky to find the answer for this. I load traffic.pcapng file in wireshark and found NTLMSSP authentication being used. So we have to decrypt the data to get results. After some research, I found this blog to move forward: Blog.
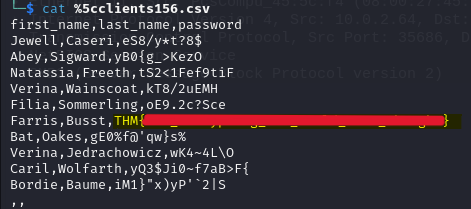
According to this blog we have to add our password in Edit -> Preferences -> Protocols -> NTLMSSP -> NT Password in wireshark. After this I found file named clients156.csv: 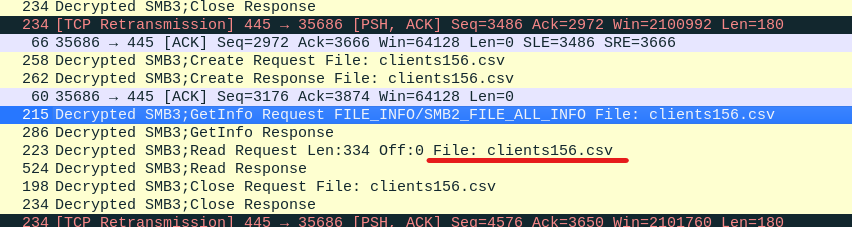
Now, we will export this file from File -> Export Objects -> SMB. Look into the exported file to get the flag:
What is the flag that the second user got access to?
For this flag, we do not have password for the second user like first user and I was not able to crack it either. I found this blog that suggests how to use NT hash to decrypt data in wireshark: Blog
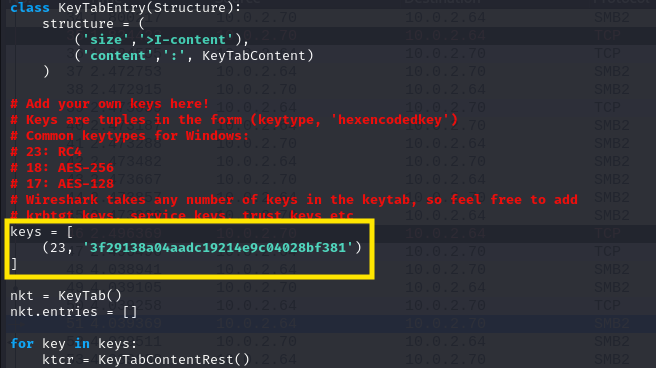
According to the blog we need to create one keytab file and load it in wireshark to decrypt traffic data. First we need keytab.py and edit it to use 23(RC4) as key type for NT hash.
Save this file and run it to get keytab file:
1
$ python3 keytab.py keytab.kt
Now, go to Edit -> Preferences -> KRB5 and load keytab.kt file. We can notice one more .csv file called clients978.csv. 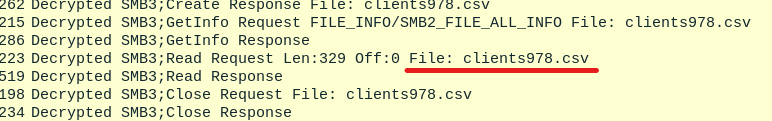
Now, export this file and read it to get the flag: